Tutorial: Password Attacks
Table of Contents
Anybody you meet will tell you that weak passwords are responsible for dozens of successful intrusions, both local and remote. As a trained network administrator or security engineer, you have counseled users to make their passwords stronger many times. What you may not be aware of is that many technology professionals make weak passwords or patterns of passwords that endanger not just their own accounts but the entire network that they maintain. This article will show you several tools for testing the passwords on your network, so you can help guide your users to the habit of better passwords.
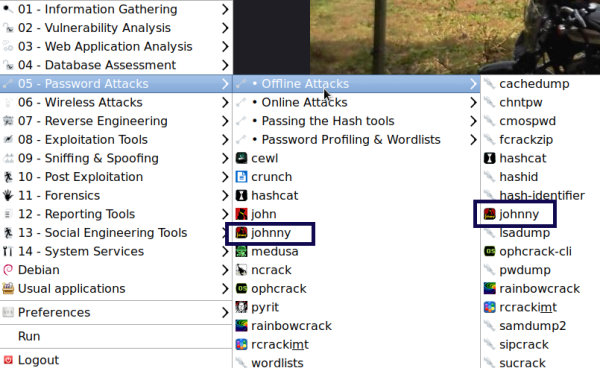
1. Johnny
First, take a look at Johnny. Johnny is a GUI frontend for John. For most password cracking tasks, this is an easy way to use John. It uses the normal defaults for most password cracking sessions. Once you have captured some hashes, save them to a text file and open Johnny.
The following is a screenshot from the LXDE desktop showing where Johnny can be found. You can also find it on all the other desktops under the same header location, Applications | 05 - Password Attacks | johnny:
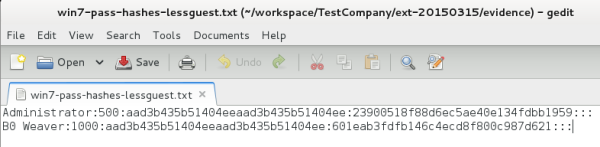
The list is shortened to only include the hashes of the two accounts that have critical access to the networked systems:
Once Johnny is open, click on the Open Passwd File button and pick the text file, where you have saved the user's hash values. This will load the file into Johnny.
Hacker's note: It is best to delete the guest and any other user account that you do not want to crack. This will cut down on the length of time it takes to crack the passwords. As you see, only two accounts are cracked.
The following screenshot is your first view of Johnny's interface, very simple and powerful:
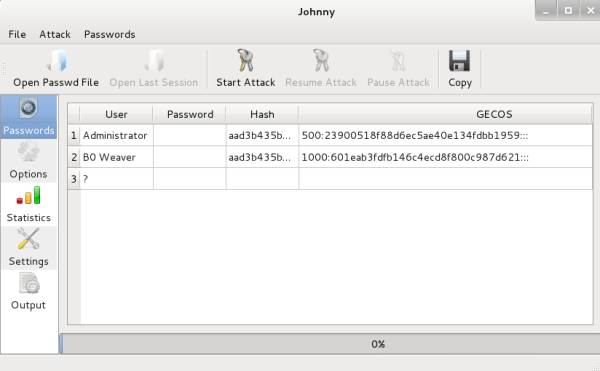
Because this is a test network, there are only two usernames in the dialog window. In a production network, there would be as many usernames as people in the organization permitted to log into the system. It is likely that at least one of these users has administrative privileges.
Hacker's note: Remember that the administrator's account is always UID 500. Sometimes, an administrator will change the name of the administrator account. This does hide the account in some cases, but once you get the UIDs of the accounts, finding the administrator is as easy as 500.
These hashes come from a Windows 7 system. With Windows 7, LM hashes are no longer used by default, so you must change the default LM hash cracking. You will get the following error in the Output tab if this is not changed:
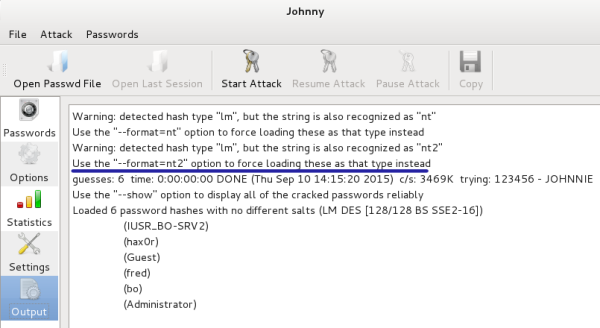
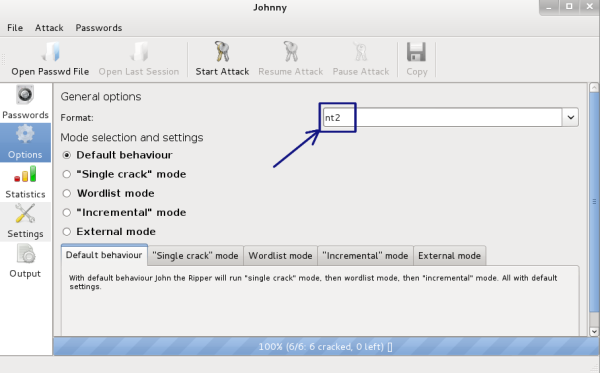
Click on the Options tab and change the auto detect to nt2, as shown in the following screenshot:
Now, click on the Passwords tab and then click on the Start Attack button. This will begin the cracking process. You can see the process in the bottom tab on the screen:
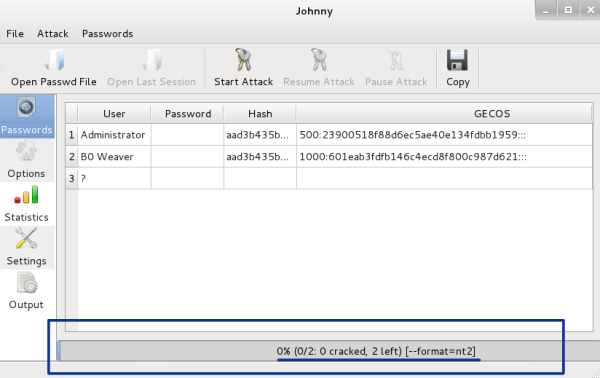
Note that it now shows the format as nt2 and is running. Have a cup of coffee. This might take a while. Also, note that you have a Pause Attack button. If needed, you can pause the attack.
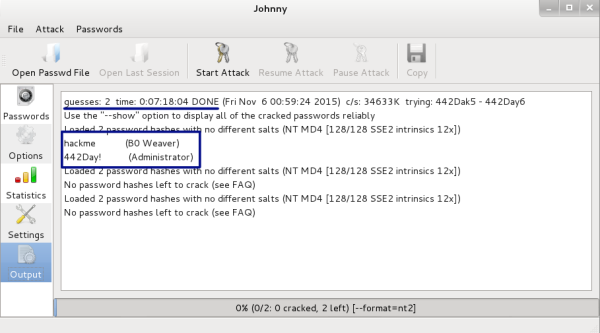
Sometimes, open source applications have quirks. Johnny is no different. Sometimes, when doing a cracking run, the process will run and crack the passwords but they will not show in the GUI window. If the Pause Attack button has grayed out and only the Start button can be clicked, the run has completed and the passwords have been cracked. You can find the information by clicking on the Options button. This page will also show you the length of time it took to run and that the passwords cracked. This the best page to get all the results of the run.
You can see in the next screenshot that it took 7 hours and 18 minutes to crack two passwords with six and seven characters, using the complexity of uppercase and lowercase letters, numbers, and special characters:
2. John the Ripper (command line)
John the Ripper is the application that underlies Johnny. You may be more comfortable on the command line than in a GUI, when using password cracking tools, such as John the Ripper. You may go for the CLI because it uses fewer resources than the GUI, or because you are working through an SSH connection to a server without a GUI interface. It is easy to use John the Ripper, and there are a lot more options and ways to use John by using the command line that has not yet been added to Johnny.
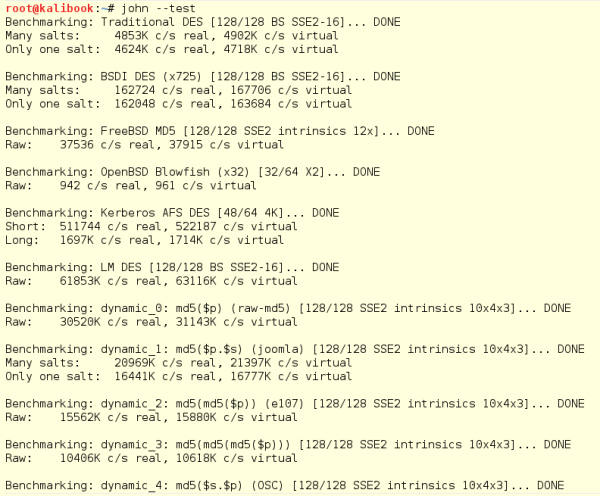
You can see all the various hashing algorithms supported by John and test the speed of your system for cracking by running the following command:
john -test
This will run through all the various hashing algorithms supported by John and give you the speed it will take for the various hashes. The following screenshot shows the read-out from the test flag:
Now, run John against a set of hashes obtained from earlier
exploitation of a system. Note the flags used to perform this. Use
--format=nt2 and then pick the file:
john -format=nt2 hashdump.txt
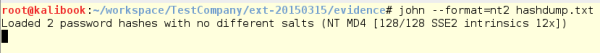
With this cracking run, you can crack passwords that are more than six characters. Note the time it has taken to run this process. This shows, when it comes to passwords, that the length is more important than the complexity.
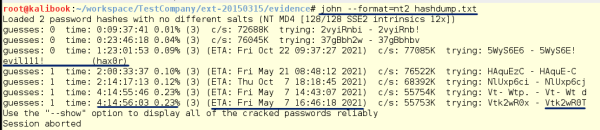
In the following screenshot, you can see that it took 1 day and 23 hours to crack a pretty simple seven-character password. The second password which was eight characters long did not crack until 4 days, 14 hours, and 56 minutes. Yes, each extra character makes the time it takes to crack grow exponentially:
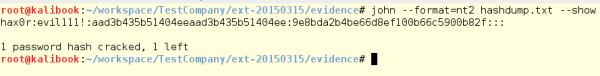
By running the -show flag after the run, you can see the cracked
word and that you have one still left to crack:
This cracking was done on a VM with one running processor. Adding processors will increase the number of running threads during cracking and that makes the job take less time. People have built machines filled with processors and GPU cards that can crack passwords in a matter of hours. Some use Amazon AWS and set up instances with a lot of processing power, but this costs a lot of money.
It's also known that some ingenious college students have fired up the college supercomputer meant for modeling the solar system and used these systems to crack passwords really fast. Even if your neighborhood evil hacker has these kinds of systems, the longer password is still better.
Systems like these are the reason for using passwords or pass-phrases with a length over 14 characters. Even with pass-phrases over 14 characters, this shows that if you have the hash, it is just a matter of time, money, and processing power before you have the password.
3. Further Reading
This article of learning about password attacks was by Wolf Halton, an authority on computer and internet security, a best-selling author on computer security, and the CEO of Atlanta Cloud Technology, and Bo Weaver, the senior penetration tester and security researcher for CompliancePoint, an Atlanta based security consulting company.
If you found this article interesting, you can explore Kali Linux 2018: Windows Penetration Testing - Second Edition to become the ethical hacker you need to be to protect your network. Kali Linux 2018: Windows Penetration Testing - Second Edition has the most advanced tools and techniques to reproduce the methods used by sophisticated hackers to make you an expert in Kali Linux penetration testing.